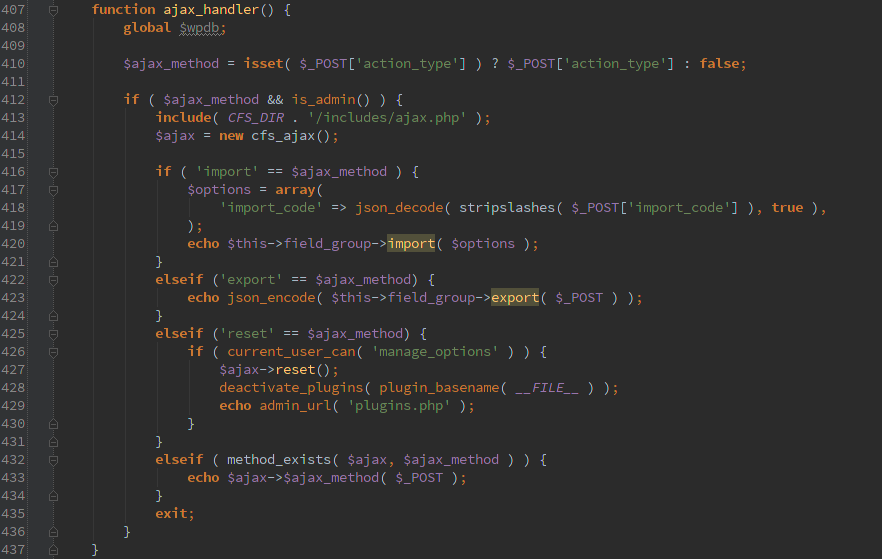
Recently I was looking at the Custom Field Suite plugin. I’d never used it before and as always before using it I had to quickly go through the code to find an obvious security issues.
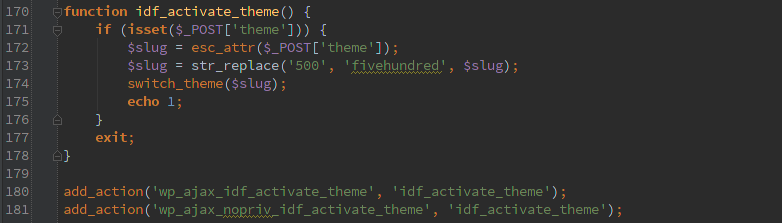
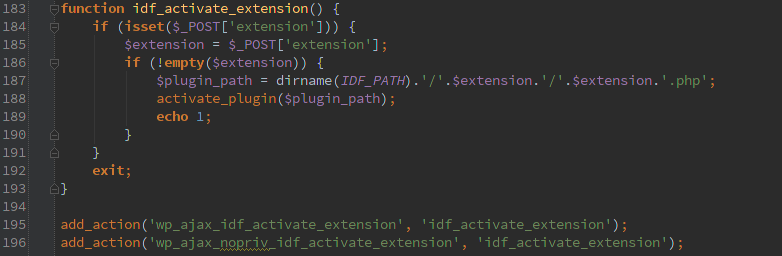
The frequent offender AJAX jumped out at me. Luckily this is not the ‘nopriv’ type, so an attacker would have to have an account on the WordPress site, but any basic account will work.
- Import custom fields
- Export custom fields
- Search for posts by title (via includes/fields/ajax.php:search_posts() )
The only AJAX function that was secured was ‘reset’ which would remove everything CFS related from the database and deactivate the plugin.
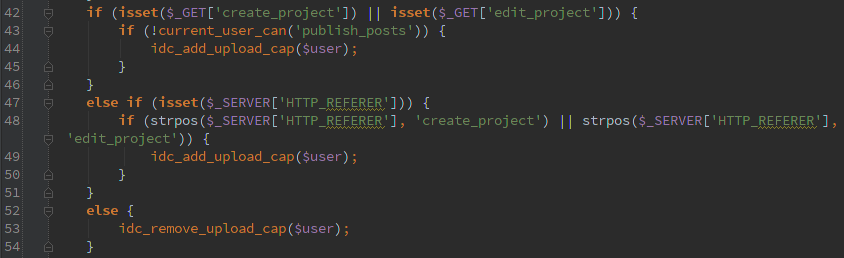
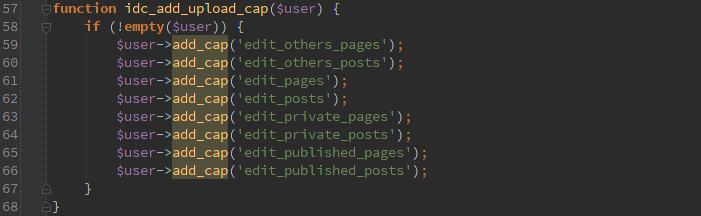
With all the awesome stuff that CFS can do, I’m sure an attacker could find something fun to do once they can export your setup and re-import it.
Matt was quick to respond and get a new version out there. Here is the Changelog. I recommend everyone update immediately.
Timeline
- 3/3/2015 12:45pm Initial disclosure email
- 3/3/2015 12:59pm Response and issue fixed in github.com
- 3/4/2015 Updated version (2.4.1) released on wordpress.org