OptinMonster is a WordPress plugin/service to collect leads from customers visiting a website. The plugin is free to download from wordpress.org and it claims there are 20,000+ active installs. The service does require a membership, so presumably they have contacted all of their customers to tell them to upgrade.
I discovered an issue that allows any non-authenticated user to execute arbitrary WordPress shortcodes. Generally this type of access is only allowed by users with the ability to edit content on a site. Most of the default shortcodes aren’t very exciting and don’t provide much leverage for an attacker, but many third-party plugins expect that anyone who is able to execute shortcodes has sufficient permission that they don’t need to provide any further security.
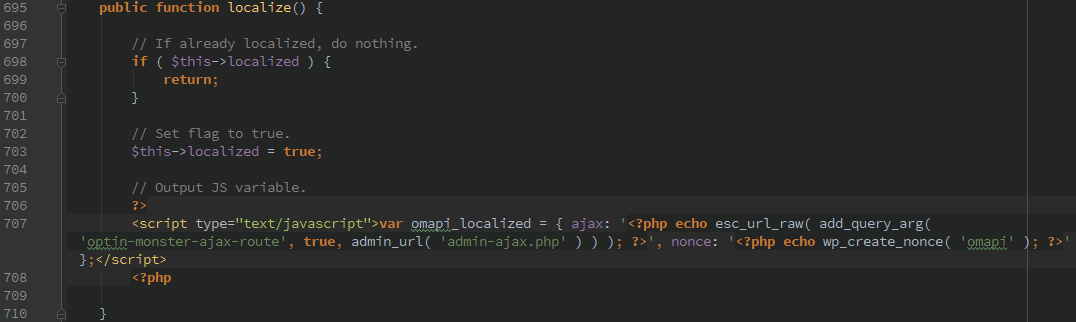
The exact function is protected by the ‘omapi’ nonce, unfortunately that nonce is leaked on any page load that calls wp_footer.
Arbitrary shortcode execution
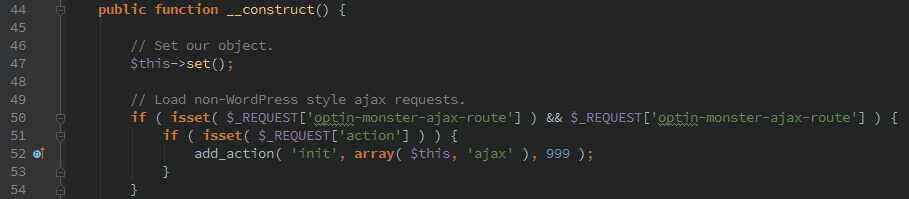
During initialization the OptinMonster plugin sets up it’s own ajax handler which will fire off on the ‘init’ WordPress action.
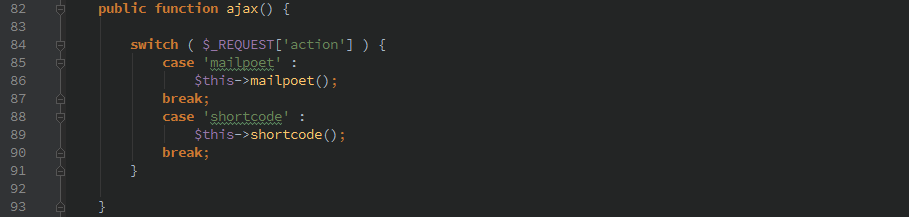
Only two ‘actions’ can be called from this function.
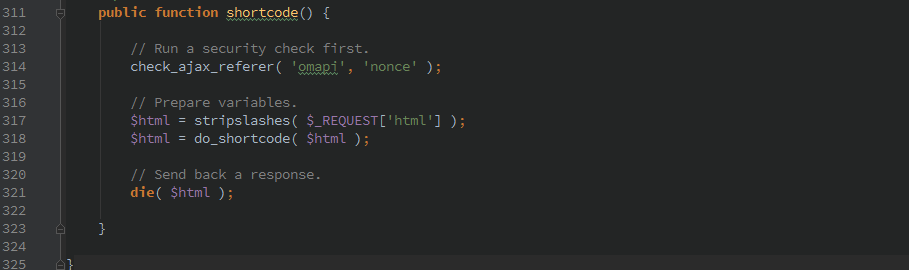
Here we see that any arbitrary user input is passed to the do_shortcode() WordPress function. At least the function is protected by check_ajax_referer() which will verify the nonce.
Unfortunately, the nonce is leaked during most page loads by the ‘wp_footer’ action.
Timeline
- 1/14/2016 12:27am Initial contact to locate responsible party
- 1/14/2016 9:15am Reply from vendor
- 1/14/2016 11:25am Initial disclosure
- 3/21/2016 Version 1.1.4.6 Released