Formidable Forms is a visual form builder WordPress plugin from Strategy 11. The free version has 200,000+ active installs which makes it one of the most popular contact form plugins for WordPress.
I noticed some potential security vulnerabilities in some of the more obscure AJAX actions they make available. Most of the actions are protected by a helpful function FrmAppHelper::permission_check() which checks if a user has the WordPress permission for the action as well as a valid nonce for the action. Kudos on implementing a system that makes it easy to be secure without duplicating code all over the place!
All of the actions uncovered require at least a valid WordPress account, but any account will work. If you are using this plugin, please update immediately.
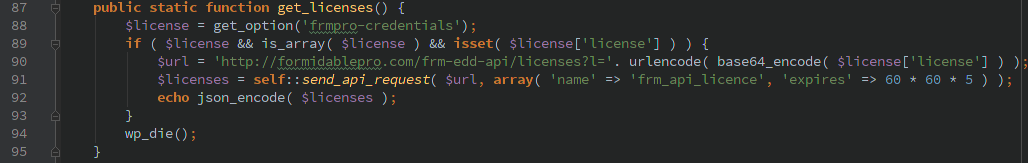
Logged in users can retrieve Addon licenses
The ‘frm_fill_licenses’ AJAX action does not check for a nonce or any other authorization, allowing a user to retrieve a list of licenses from the formidablepro.com API with the hosts credentials.
frm_ajax Nonce leak
The other vulnerabilities below do require a valid nonce, though I did discover a location the ‘frm_ajax’ nonce was leaked out to a logged in user without proper authorization. I’m not going to reveal the method to retrieve it, but it was readily available.
Modify Form Fields
Using the leaked ‘frm_ajax’ an attacker is able to call many of the AJAX actions related to editing the forms. Without going into too much detail here, I was able to inject unfiltered javascript into an existing form that would be displayed to users.
Timeline
- 2/2/2016 Tried multiple contact emails to reach someone
- 2/3/2016 Located form on strategy11.com to try to use to contact
- 2/3/2016 11:46am Received response from developer
- 2/3/2016 11:59am Full disclosure sent
- 2/9/2016 Issues fixed in github repository
- 2/12/2016 Updated version released to wordpress.org repository