Beaver Builder is a popular WordPress plugin that allows drag & drop editing of pages. I’m a big fan of this plugin it allows users to make some pretty great sites without a lot of work. Any plugin I’m going to use I have to do at least some minimal reading of the code to search for security issues. I discovered a few issues here, though what I did discover requires a valid WordPress user account (not just admin) to use them.
The wordpress.org page for the lite version claims there are 50,000+ active installs, I could not find any indication of how many users of the pro version there are.
Unauthorized AJAX Calls
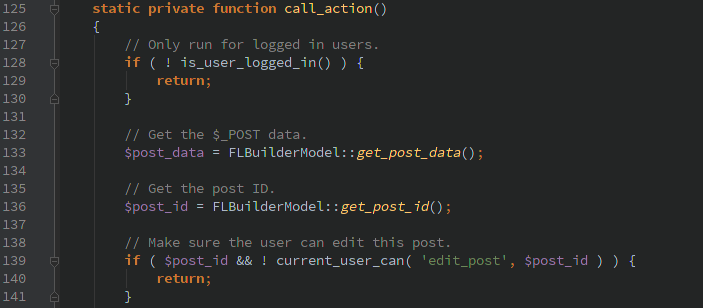
The Beaver Builder plugin creates it’s own AJAX handler that is hooked into the ‘wp’ WordPress action.
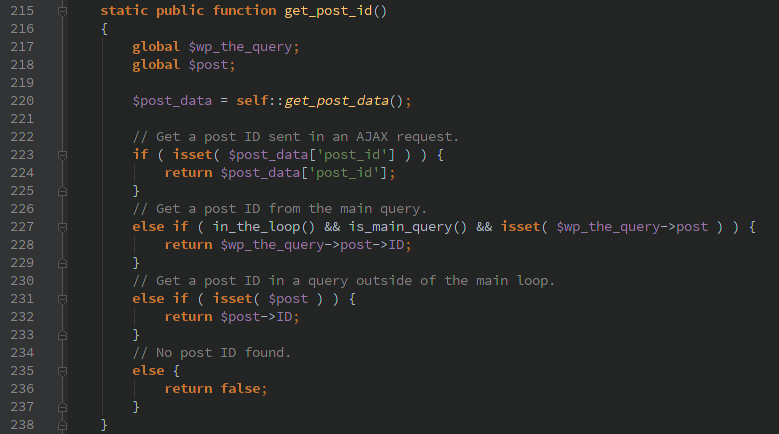
This looks solid at first glance. It requires a user to be logged in and also checks that the current_user_can() edit this post. Unfortunately as seen below, FLBuilderModel::get_post_id() allows passing the ‘post_id’ via HTTP POST data (abstracted away behind the self::get_post_data() function). A user is able to pass in HTTP POST ‘post_id=0’ and the current_user_can() function call is never run.
After a nefarious user circumvents those checks they are able to call any of the 40+ actions that Beaver Builder includes. Which would allow them to create/edit pages, manage services, list all users.
Timeline
- 1/19/2016 3:30pm Sent request for contact information
- 1/19/2016 10:54pm Response received
- 1/20/2016 12:02am Security disclosure sent
- 1/24/2016 Updated version released