The WordPress plugin Simple Download Monitor has a few security vulnerabilities that allows unauthenticated users to list all uploaded files, delete thumbnails associated with them, and uploaded files with password protection can be download without entering a password.
As of 1/19/2016 the wordpress.org information says there are 10,000+ active installs of this plugin.
The vendor Tips and Tricks HQ has released version 3.2.9 to resolve this issue.
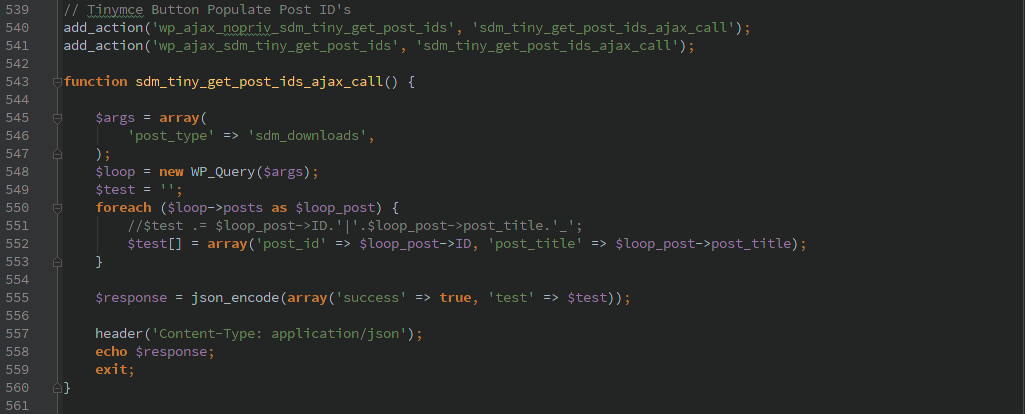
List all uploaded files
Unauthenticated AJAX allows any user to access the ‘sdm_tiny_get_post_ids’ action which will return a JSON encoded list of all ‘post_id’ and ‘post_title’ that were uploaded with the Simple Download Monitor plugin. In many cases these files are publicly visible already so this isn’t a major security issue in most cases.
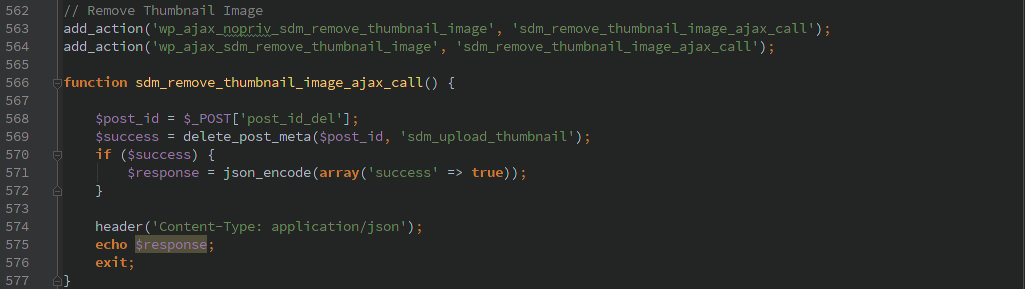
Delete thumbnails
Unauthenticated AJAX calls again allow any unauthenticated user to delete thumbnail images that were added using this plugin via the ‘sdm_remove_thumbnail_image’ action.
Download files without password protection
This is the biggest security issue here, they do provide an AJAX command that verifies the post password to allow downloading the file but there is also this backdoor method to access the file that can be used without any password verification. Though the access is logged if logging is enabled.
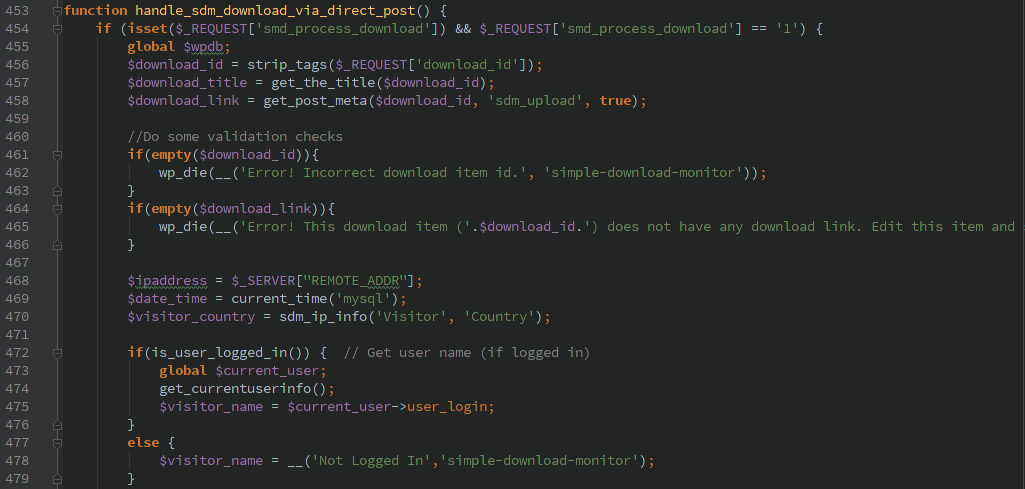
Early on by the ‘init’ action the handle_sdm_download_via_direct_post() function is called. Which then takes the supplied ‘download_id’ and retrieves the post containing a file.
After the bit of logging it finally happily redirects the user to the proper download URL.
One additional note, these files are not actually password protected, just the posts that contain them. So if someone has the direct URL to a file they can download it without any further authorization.
It’s always wise to ensure that any request is properly authorized.
Timeline
- 1/12/2016 2:16pm Initial contact email sent to find appropriate security/developer contact
- 1/12/2016 10:16pm Vendor responds with contact information
- 1/13/2016 10:16am Complete disclosure sent
- 1/14/2016 7:31pm Vendor reply stating they are working on issue and requested more information
- 1/16/2016 7:37pm Vendor reply stating a new version has been released