There is a serious security vulnerability in All-in-One WP Migration version 2.0.4. Update immediately. This vulnerability can allow users without any authentication to export a copy of your database, plugins, themes, and uploaded files.
My story
It wasn’t supposed to happen like this. I was setting up a couple of test servers for a project I’m working on and I wanted to be able to backup and move the data around easily. Why not try out one of the tools designed to do this rather than roll my own?
I found All-in-One WP Migration, with 40,000+ installs it should be solid. Of course, I couldn’t just install it and use it as is. I had to pull back the curtain and take a peek.
At first, I saw our familiar friend AJAX without proper protection, but the import call actually checked permission. The other exposed AJAX calls couldn’t really do anything useful/threatening.
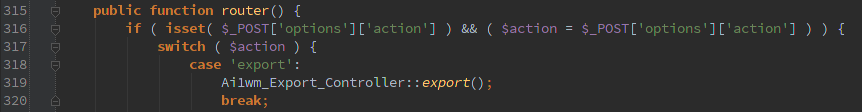
Then I noticed this little gem:
Could be benign as long as it’s called from some place that has some form of authorization. Unfortunately it is called from the ‘init’ action.
Luckily the import function is protected so you can’t make any changes, but there is plenty of fun stuff that can be exported.
Just having access to the database should be enough to panic any site administrator, but having all of the uploads, themes, and plugins bundled up in a zip file is terrifying.
I will not distribute a PoC for this. Please upgrade your sites immediately!
Vendor Response
ServMask was very quick to respond and was planning on releasing an update asap. I suggested they contact plugins@wordpress.org and see if there is the possibility to have the plugin force updated like the Yoast WordPress SEO plugin update was last week.
Timeline
- 3/12/2015 2:40pm Vendor contacted
- 3/12/2015 2:47pm Vendor response
- 3/14/2015 Update released on wordpress.org